
The cost of cybersecurity spending in 2017 represented $86.4 billion according to Gartner and is expected to exceed $1 trillion in over the next five years.
At a very alarming rate, projections show that cybercriminals will impact 6 billion people by 2022. Consequently, in the corporate world, Ginni Rometty, IBM's president and CEO, said, "Cybercrime is the greatest threat to every company in the world."
Ransomware attacks have become a common practice by cybercriminals, exploiting the fact that most entities or users do not possess a comprehensive backup of their valuable data. These attacks encrypt information and demand a ransom in the form of bitcoin or other cryptocurrencies to release the decryption key

The traditional security tools used to protect a computer system such as anti-virus software is useful in detecting known viruses and malware but they do not strengthen the core cybersecurity posture of the operating system. Integrated or external network firewalls also provide additional port filtering mechanisms for communication sockets, but they do not address the hundreds of system settings at risk of being exploited if not correctly configured.
The most crucial component in establishing military-grade cybersecurity, is to start with a system baseline that provides the most restrictive environment without compromising system performance or functionality.
At PC-WARRIORS we have mastered this crucial component with our proprietary tools, resulting in military-grade cybersecurity without loss of system performance or functionality.
Our RMF-DASHBOARD continuous monitoring solution is the cornerstone of the continuous monitoring program for dozens of federal contractors throughout the US.
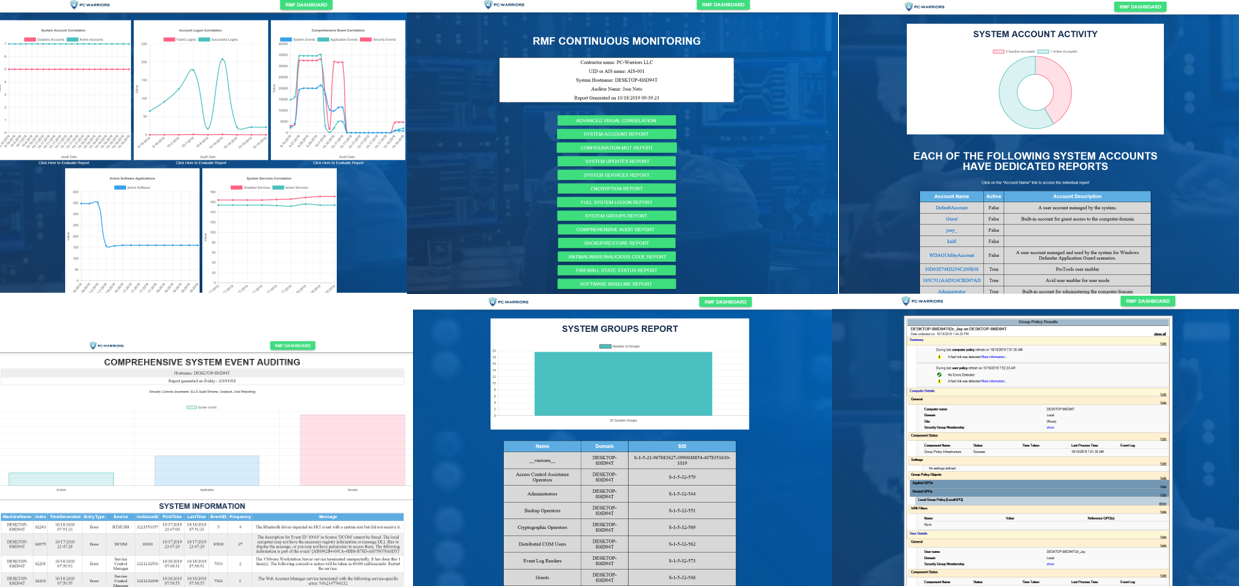

By developing a Comprehensive/Holistic approach to Cybersecurity Defense, our services encompass a multi-layer customizable approach of protection for large organizations, small business owners, or an individual.
By conducting an in-depth Vulnerability Assessment, we are able to identify an organization's current cybersecurity posture. This assessment represents the first layer of information gathering and sets a baseline for improvement.
During this process, we will assess all connected computing nodes, all network peripherals, and devices. The scope of the assessment also includes the analysis of operating systems, third-party applications, vendor firmware updates, and other published vulnerabilities.
Upon completion of the assessment, the PC-Warriors vulnerability assessment report (VAR) will be produced, identifying any vulnerabilities and potential attack vectors discovered that are at risk of being compromised.
Utilizing the VAR, we conduct Penetration Simulation/Testing which simulates the exploitation of the discovered attack vectors and provides a more detailed report identifying the severity of exploits.
This aggressive testing approach may momentarily disrupt daily operations to measure the impact of possible attacks, providing the organization with a realistic impact analysis of their system’s infrastructure status.
Through additional testing of the discovered vulnerabilities, this process eliminates false/positives and delivers a more concise and detailed report of eminent threats.
Due to the lack of cybersecurity awareness, some of our clients make initial contact with us after they have been compromised. When this occurs, there are many critical steps that must be considered. Our first priority is to identify the incident and determine the level of severity and the impact to an organization’s operational status.
The initial objective is to restore the organization to normal operational status. This is accomplished by working closely with the organizations designated staff and disaster recovery procedures.
Should the incident be deemed critical, our team of compliance experts, would perform an in-depth assessment/investigation of the incident and notify the appropriate officials. Any evidence from the attack must also be preserved through proper chain-of-custody procedures to preserve its forensic integrity for legal proceedings.
The attack vector used must be analyzed to prevent future and/or repeated exploits through a careful analysis of injected malware or malicious scripts.
Behind every cyberattack, there is always a human element and motive. We provide a range of cybersecurity training specifically developed for system administrators, executive leadership, and end-users within an organization or entity.
Basic Cybersecurity Awareness training
Technical Best-Practices on maintaining a secure IT Infrastructure
Executive Cybersecurity Top-Down leadership planning
Risk Management Framework (RMF)
Our founder has personally trained enlisted and Officer ranks in all US Military branches for DoD 8570 compliance

With the emergence of Risk Management Framework (RMF), and the Cybersecurity Maturity Model Certification (CMMC) , federal contractors are required to maintain a resilient cybersecurity posture.
Our compliance experts will assist you in meeting the expected government compliance baseline rules and regulations.
Given the increase of Advanced Persistent Threats (APT) in cyber space, experts concur that continuous monitoring and protection are needed to minimize the risk of exploitation. PC-Warriors is prepared to design, develop and implement a continuous monitoring plan for your organization’s security needs.
As digital identities become more and more valuable in our society, High-profile individuals or influencers have become targets for organized cybercrime. At PC-Warriors we provide Expert Digital Identity Protection tailored to meet our client’s requirements. We understand the balance between productivity and security in accordance with appropriate fit for purpos,e risk mitigation and contingency support
PC-Warrior’s World class security professionals are drawn from various elite backgrounds, they include former Military and Intelligence experts.

Our team of expert cybersecurity professionals led by Dr. Jose Neto (Former DoD INFOSEC Special Agent) diligently work around the clock staying up to date with the latest vulnerabilities and countermeasures
Recepient of the DSS Director's Coin award for his innovative SSP-Helper Software solution to expedite the processing of C/A packages.
